Physically Unclonable Function (PUF) IP
A hardware-based solution that exploits the variations inherent in the device to produce a unique, unclonable response from the device to a given input
Devices are much more connected with IoT and require authentication and identity for security purpose, such as protecting untrusted access to a cloud by a counterfeited device.
Authentication requires keys that must be embedded in devices. The traditional method is to store these keys in cryptographic chips, OTP components (one-time password) or non-volatile memories. The concern is that the stored values can be retrieved and copied using various means such as:
- Memory read-out advanced techniques;
- Reverse engineering techniques;
- Physical attacks such as Probing.
The solution to address these points is to use silicon extracted keys that are generated by a PUF. This distinguishing feature offers real protection against reverse engineering techniques
Physical Unclonable Function or Physically Unclonable Function (PUF) is known to be a solution for anti-copy applications at a silicon level. However, as they are sensitive components, they are the obvious target of physical attacks. Thus, they shall be well protected.
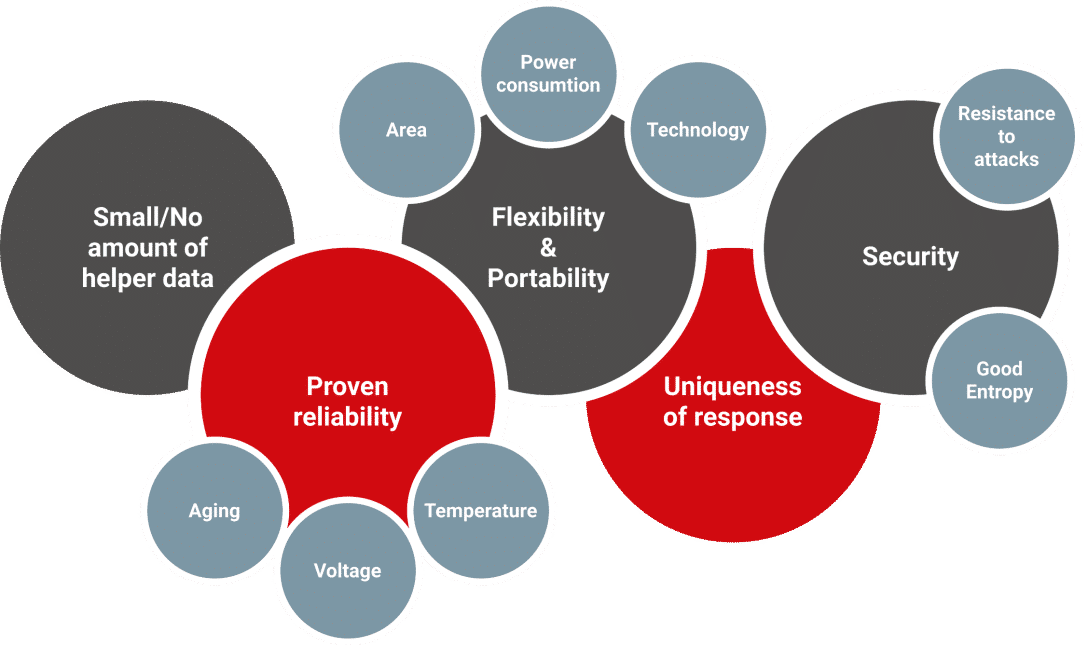
In order to have a good PUF, many parameters must be taken into account such as:
- Randomness, which indicates the balance of 0 and 1
- Steadiness, which indicates he stability with which a PUF produces the same responses to the same sets of challenges.
- Diffuseness, which indicates the degree of difference between the IDs generated from the different challenge sets in the same PUF
- Uniqueness, which indicates how different the generated IDs are.
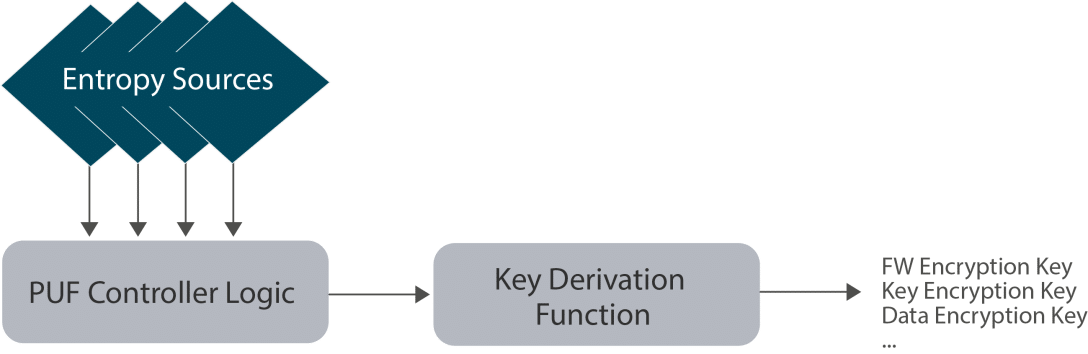
A PUF is composed of two main components:
- Set of PUF entropy source based on loop, which exploits electronic noise to provide raw random bits
- PUF Manager, which controls the PUF entropy sources by giving them various challenges. The measurements returned by the PUF entropy sources are processed by the manager to generate the key.
Secure-IC has developed a strong key generation with a Loop PUF in order to ensure
- The availability of a stochastic model
- A stochastic model explains and gives proofs of the quality of entropy and reliability of the PUF.
- A good entropy
- It is important that the PUF response has a good entropy to be used as a key. Indeed, a good cryptographic key is a mix between ‘0’ and ‘1’.
- Embedded functional self-tests
- It is important to validate the integrity of the PUF before using it for example by using health-tests or BIST (built-in self-test)
- Security countermeasures
- The PUF embeds countermeasures against several types of attacks such as side channel attack, fault injection attack, etc.
- Proven reliability regarding PVT variations
- PUF outputs are stable under all operating conditions
- A proven reliability regarding aging
- The key generated by the PUF is stable throughout the life of the system.
- Flexibility in terms of area, power consumption and latency
- Portable on many different technologies
Physically Unclonable Function IP is particularly relevant for:
- Fingerprint of the device, it allows precise identification of a chip. This ID should be member of a valid list.
- Use the output as part of a cryptographic parameter. The PUF response may be used as a cryptographic key
- The PUF is used as part of a private/public key generator. These keys are then used in authentication protocol.
- The PUF response is used as the master key (Root Key) of the system to encrypt and authenticate the firmware. The firmware is decrypted and authenticated during the Boot before to being loaded.
Physically Unclonable Function IP offers the following benefits:
- RAM-Free PUF
- Possibility not to depend on helper data
- Aging, temperature and voltage evaluation
- A complete set of build-in countermeasures against various attacks:
- Attack-proof by design completed by a full set of countermeasures
- Ready to go in the wild and protect your device and assets for any type of application
- High entropy reduces collision probability
- Each device is truly unique
- At every stage of design, levers are available to ensure reliability and entropy levels
- Highly adaptable to any design kit, with safeguard measures to ensure proper functioning
- Pre- and post-silicon tuning of the PUF parameters to fit every application and every condition
- Possible action at each step to avoid any need of re-engineering
- Highly secure solution for key provisioning. The Key is generated inside the chips using the PUF and is not stored in memory
- Silicon Proven
Secure-IC is member of the Technical Committee ISO/IEC JTC 1/SC 27 which works on ISO/IEC 20897 Security requirements, test and evaluation methods for physically unclonable functions for generating non-stored security parameter.
More information about our support to security certification and compliance