Transport Layer Security (TLS) is perhaps the most well-known cryptographic protocol. It is used for providing communication in a large variety of applications security including secure web browsing. Typically, web browsers show a lock icon next to the URL link when it is using the protected HTTPS protocol; this means that the communication is protected with TLS. Although secure web browsing is the most visible application of TLS, it is nowadays used in a large variety of different applications including also machine-to-machine communication protocols.
The history of TLS dates back to the 1990s. It was developed by Netscape Communications and was originally called Secure Sockets Layer (SSL). TLS 1.0 was released as RFC 2246 by the IETF (Internet Engineering Task Force) in 1999. The early version of both SSL and TLS suffered from severe vulnerabilities and they are no longer recommended to be used. Nowadays, basically two version of TLS are in mainstream use: TLS 1.2 defined in RFC 5246 from 2008 and TLS 1.3 defined in RFC 8446 from 2018. The latter includes significant security and performance improvements over the earlier versions and is the recommended version for any new systems.
TLS Handshake – how does it work?
TLS involves two parties: a client and a server. A TLS session is initiated by the client and it begins with a TLS Handshake. During the Handshake,
- the client and server agree upon the cryptographic algorithms that are used in Handshake and the communication;
- the client and server exchange a shared secret key that later is used for protecting client-server communication;
- the client authenticates the server by using the server’s certificate; and
- optionally the server also authenticates the client by using the client’s certificate (however, it is more common that if client authentication is needed, then it is done with a separate protocol over the established TLS session);
When the TLS Handshake has been finished successfully, the main communication is protected for both confidentiality and authenticity/integrity by using the shared secret key. Most commonly the communication is nowadays protected using the AES-GCM authenticated encryption scheme, but other alternatives are also possible (for example, ChaCha20-Poly1305 or AES-CBC + HMAC).
New post-quantum winds
The most significant new thing in contemporary cryptography is the shift to Post-Quantum Cryptography (PQC). The traditional asymmetric (public key) cryptography methods RSA and Elliptic Curve Cryptography (ECC) are vulnerable to quantum attacks if large enough quantum computers become reality. PQC are algorithms that are not affected by the emerging quantum threat and are eventually to be used as replacements of the current RSA and ECC.
Various standardisation bodies and government authorities are currently setting standards and requirements for shifting to PQC in practical systems. Most importantly, the American NIST has been running a standardisation process for finding secure and efficient PQC algorithms for key exchange and digital signatures. In summer 2022, they concluded the selection process and announced four algorithms – one for key exchange and three for signatures – that are to be included in the first PQC standard. The key exchange algorithm is called CRYSTALS-Kyber and the primary signature algorithm is called CRYSTALS-Dilithium.
Being new, PQC algorithms have not yet reached the same level of confidence in their security that, for example, RSA and ECC have. As a consequence, it is generally recommended not to directly replace the traditional algorithms with the new PQC algorithms but, instead, use a hybrid solution where the security relies on both ECC and PQC. In such a hybrid solution, PQC offers protection against future adversaries that may be able to leverage quantum computers in attacks, and ECC provides fallback security against possible, yet unlikely, failures of PQC algorithms under more traditional cryptanalytic attacks.
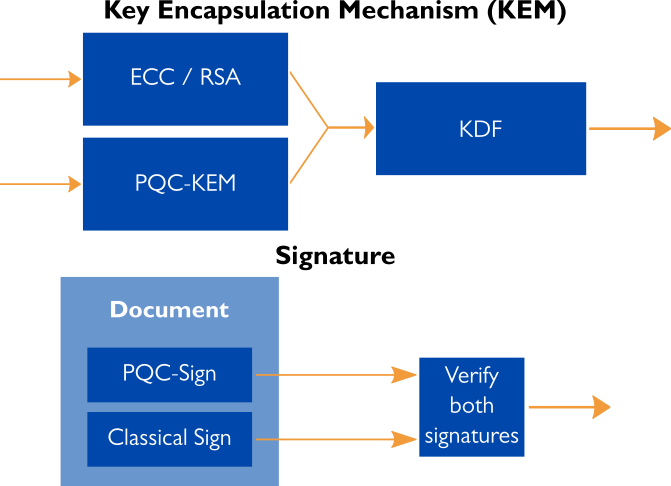
Enter Post-Quantum TLS
Both the key exchange and server (and client) authentication of TLS Handshake rely heavily on the use of asymmetric cryptography and, nowadays, especially on ECC. Thus, the security of the TLS Handshake as defined in TLS 1.2 or TLS 1.3 is affected by the quantum threat, and there must be a roadmap for adopting PQC algorithms in TLS.
Indeed, the work for Post-Quantum TLS (PQ-TLS) has already began: for example, Stebila (Univ. Waterloo), Fluhrer (Cisco), and Gueron (Amazon Web Services) have published an internet draft describing the use of hybrid key exchange in TLS 1.3. They describe a scheme for using two (or more) algorithms in TLS 1.3 key exchange in a way that the security of the TLS Handshake remains secure as long as one of the algorithms remains unbroken. A natural application for their scheme is to combine a PQC algorithm with ECC in order to implement an aforementioned hybrid solution. They propose four such combinations in their draft, where different elliptic curves are combined with CRYSTALS-Kyber. These combinations and their different key lengths are targeted for various use cases depending on their communication bandwidths and other requirements.
It is noteworthy that the above proposal is only for key exchange, and it does not propose anything for authentication (that is, digital signatures). The motivation for this is that the proposal suggests a protection method against future adversaries and assumes that quantum attacks are not possible today. Hence, TLS session needs to be protected against adversaries who record session communication so that they could later break the security with a quantum computer and find out what was being communicated. Such an adversary could break the confidentiality protection of the TLS session by finding out the shared secret key by breaking ECC with a quantum computer, but breaking authentication retrospectively would not help the adversary because the session would have been closed long time ago.
TLS and Post-Quantum Cryptography: Securing Communications Today and Tomorrow
Xiphera’s webinar TLS and Post-Quantum Cryptography: Securing Communications Today and Tomorrow explores the use cases of TLS applications as well as the ongoing efforts to take Post-Quantum Cryptography (PQC) into use in TLS 1.3. The important and timely topics are presented by Mr. Mark Frost, FPGA Security and 5G Technical Marketing Manager of Intel Corporation, and Dr. Kimmo Järvinen, Co-founder and CTO of Xiphera.
Watch the webinar recording here.
If you want receive information about Xiphera’s upcoming webinars, sign up for Xiphera’s webinar subscription list here, and you’ll never miss any of our fascinating webinars!
Find all episodes of Xiphera’s webinar series Cryptography under the hood here.




