Hardware root key generation and storage that never leaves the chip
PUFrt includes a 1024-bit physical unclonable function (PUF) and a true random number generator (TRNG) complying with the NIST SP800- 90B/SP-800-22 standard specifications. These features aid in the encryption/decryption requirements of sensitive information and data, achieving a higher level of data security protection. Furthermore, an additional 8k-bit secure storage space with PUF is provided for the key or sensitive information injected by the customer, which makes the original security and NeoFuse OTP more resistant to physical attacks.
The rising risks from the IoT are limiting its potential. For perspective, it takes, on average, only five minutes for a deployed IoT device to receive its first attack. The answer is creating a collaborative security ecosystem, drawing from the safest Hardware, Software, and Operating System solutions. PUFrt can protect and connect this ecosystem at the hardware level using PUF-based encryption and authentication.
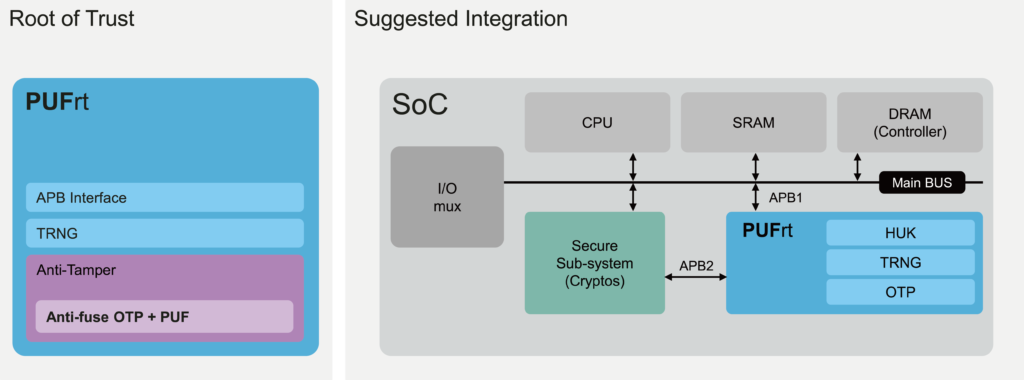
PUFrt’s Hardware Root of Trust is ushering in a new era of semiconductor security with its combination of secure Hard Macros and Digital RTL. PUFrt design includes a PUF-based 1024-bit identification code, Zero Touch key provisioning, intergrade entropy sources, secure OTP, and anti-tamper shell all in one unit. It can be integrated across a wide array of different architecture and support various operations, from lightweight hardware security key provisioning to fully functioning Crypto Coprocessors.
We lead the field in terms of platform availability, and through our parent company, eMemory, we draw from over 20 years of experience partnering with foundries and delivering high-quality IPs.
Application
PUFrt is a Hardware Root of Trust (HRoT) from PUFsecurity, offering the essential features to establish a trusted foundation for all security operations (such as secure boot). Providing the flexibility for users to select only the cryptographic engines their designs need, PUFrt can be integrated into various systems. Some usage examples include:
- Secure OTP to safely store sensitive data such as keys and boot code
- Key provisioning that enables simultaneous multi-chip key provisioning for cost reduction
- Entropy source for cryptographic engines and secure operations
Features
- Built-in standard APB controller with privilege control to create secure/non-secure separation. Additionally, interface customization is available for different design requirements.
- Four 256-bit hardware PUF chip fingerprints, include a self-health check that can be used as a unique identification(UID) or a root key(seed).
- High-quality true random number generator (TRNG)
- 8k-bit mass production OTP with built-in instant hardware encryption (customization available)
- Comprehensive anti-tamper designs in both Digital RTL and Hard Macros
Additional Features
- Autoload: Automatically send trim parameters from OTP upon power-up.
- Secure Boot: Ensure the device only boots up with the authenticated software.
- Secure Debug: Ensure robust protection against potential backdoor attacks through the Debug Access Port (DAP)
