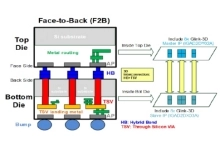
Universal Chiplet Interconnect Express (UCIe 1.0) Controller
You must be registered with the D&R website to view the full search results, including:
- Complete datasheets for software implementation for hardware root of trust software to create wrap and manage keys products
- Contact information for software implementation for hardware root of trust software to create wrap and manage keys Suppliers
Software implementation for hardware root of trust software to create wrap and manage keys Software IP Listing
| 2 Software IPs |
IP Provider: Give the best exposure to your IPs,
by listing your products for free
in the world's largest Silicon IP catalog (6 500 products from more than
400 companies)