By Albert Jeng, PUFSecurity
The Tale of TPM
The rising security threats endangering our connected world, from the chip to the cloud, are among the biggest challenges facing us today. Microsoft recently addressed some of these concerns by mandating the inclusion of TPM 2.0 (Trusted Platform Module) in all devices running its latest Windows 11 operating system. It’s a significant step towards standardizing chip-level protection and recentering the semiconductor industry to make security integral to the chip-design process.
TPM is an international standard for secure crypto coprocessors that store and protect encryption keys, passwords, and other sensitive data such as digital certificates. Since 2007, the U.S. Department of Defense (DoD) has required all newly procured computer assets to include a TPM. The International Organization for Standardization and the International Electrotechnical Commission (ISO/IEC) standardized TPM in 2009, and the Trusted Computing Group (TCG) maintains improvements of the standard.
Implementation of a TPM remains optional for device manufacturers and can range from software emulation or firmware to discrete chips. However, for security operations requiring the use of keys, most agree that a discrete TPM chip provides the highest level of security. This is particularly so for protecting critical system applications against sophisticated hacking attacks [1].
Even when TPM is implemented in hardware, a dedicated microcontroller without proper protection, for instance, can still be prone to various attacks. These tampering techniques can include side-channel attacks and exploitation of weak key generation vulnerabilities, among others. [2, 3]
Advances in TPM 2.0
While this new version makes several advances, all of us who manufacture or use online devices expect TPM to prevent critical system failures that may seriously impact safety or security. In summary, TPM1.2 and TPM 2.0 include the following functionalities [4, 5]:
- Secure storage of keys (especially endorsement keys) and attack-resistant certificates.
- Secure generation of Identifiers (IDs) and keys
- A high-quality hardware random number generator (RNG) in order to fulfill 1.
- Public-key cryptographic algorithms capable of generating and verifying digital certificates
- Symmetric key cryptographic algorithms for data encryption and decryption
- Key management all the way from endorsement key (EK) and storage root key (SRK) to session key uses.
- Secure attestation service for device management.
It is important to note that the EK’s very existence allows TPM to authenticate hardware devices. An EK programmed into a TPM chip during production is unique to each device. As such, with a solid unique identifier (UID), the TPM chip becomes a “gatekeeper” for platform authentication.
With TPM 2.0, upgrades have enhanced both security and flexibility. In addition, it fixes the one-size-fits-all ideology of TPM 1.2 by allowing platform-specific options. Notable changes include:
- A more up-to-date list of approved algorithms. For example, Elliptic Curve Cryptography (ECC) and (Secure Hash Algorithm) SHA-2 256 are included.
- Vendors can add TCG-approved (Trusted Computing Group) algorithms according to regional regulations, e.g., SM2, SM3, and SM4.
- Improved key management features from key generation to storage.
While the added crypto algorithms improve security in terms of computational difficulty, their addition does not mean that data, keys, or credentials are safe. Hackers may use several types of attacks to extract keys and sabotage devices protected by TPM. Therefore, hardware implementations of TPM 2.0 should be designed, built, and evaluated for the highest level of security against tampering attacks.
PUFcc to the Rescue
PUFcc, an intellectual property suite from PUFsecurity, is a new high-security crypto coprocessor that offers a TPM 2.0-ready security solution for critical system applications. It comes with an identification code generated by a physical unclonable function (PUF) as well as a robust, secure boundary based on the physical separation of hardware and cryptographic algorithms.
PUFcc provides the following functionalities required by TPM:
- Secure one-time programmable (OTP) memory for data and key storage with complete anti-tampering design (e.g. against invasive, semi-invasive, and non-invasive attacks).
- Inborn and unique ID plus self-generated keys inside a chip for security services.
- A NIST SP 800-90B compliant PUF-based true random number generator (TRNG) allowing high-quality dynamic entropies.
- A complete set of NIST CAVP-certified algorithms, hardware accelerator, and OSCCA / RFC standard algorithms as well.
- Firmware and application programmer’s interface (API) support for secure boot, transport layer security (TLS), and other key management operations.
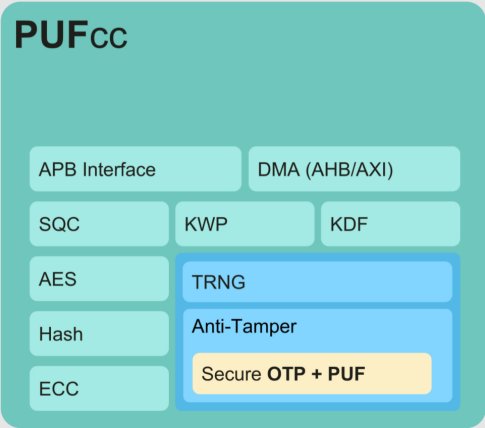
Figure.1: The design architecture of PUFcc
The PUFcc crypto coprocessor perfectly fits the upgraded TPM 2.0 standard. Furthermore, it is flexible by design, as the crypto algorithms are customizable to accommodate regional standards such as those created by the Office of State Commercial Cryptography Administration (OSCCA) in China.
Adding PUF to the Mix
As mentioned earlier, TPM standards don’t have specifications regarding functions such as secure storage. While most TPM implementations incorporate OTP memory storage as their root of trust, the PUF technology in PUFcc simplifies product deployment while also achieving an outstanding security level.
Before products with TPM can operate in the field, a crucial and costly step is to inject an EK. The EK in a TPM may well decide the security of the entire product. In one case, a chip designer must adopt onerous key-injection procedures requiring personnel and environments that have security clearance. With PUF, a chip has a unique ID and keys, eliminating the need for certified personnel and work environments to inject EKs in chips.
The uniqueness of a PUF helps simplify the early stage of a product lifecycle and safeguards the product moving forward. The key generation and certificate/key storage required by TPM (e.g., EK and root key) may benefit from such characteristics. While it is already common to store critical security parameters in OTP, PUFcc takes it up a notch by introducing chip-unique PUF-based storage protection. This makes PUFcc an excellent root of trust suitable for TPM2.0, based on the parameters.
PUF is also utilized as another layer of protection that enables many anti-tampering techniques. That is why the OTP/PUF root of trust combination serves as a firm foundation for PUFcc. First and foremost, secure storage should withstand probes by electron microscopes, focused ion beams, and other reverse engineering measures.
PUFcc is also protected against other techniques like voltage contrast, voltage glitch, power analysis, or fault injections aimed at compromising the device’s security unit. Access to sensitive data or keys is strictly controlled in case of unintended information leaks. The PUFcc OTP/PUF macro takes into account all of the above by applying the randomness of inborn PUF and PUF-based TRNG, significantly raising the bar for malicious hackers.
Recommendations
PUFsecurity provides PUFcc as an affordable, powerful, and flexible crypto coprocessor with an extensive secure boundary that’s easily designed into a discrete TPM 2.0 chip.
PUFcc enables the creation, storage, management, and secure usage of cryptographic keys. Furthermore, it supports TPM 2.0 cryptographic algorithms (NIST, OSCCA, RFC) that are compliant with modern hardware and includes comprehensive anti-tampering designs. PUFcc is the perfect fit in a critical system for safety or security of the highest level — TPM 2.0.
References
- Trusted Computing Group (TCG), “TPM 2.0: A Brief Introduction”, June 2019
Trusted Platform Module 2.0: A Brief Introduction | Trusted Computing Group - Lorenzo Franceschi-Bicchierai, “Researchers Say AMD Processors Have Serious Vulnerabilities and Backdoors,” VICE March 13, 2018.
Researchers Say AMD Processors Have Serious Vulnerabilities and Backdoors (vice.com) - Daniel Moghimi, et al., “TPM-Fail: TPM meets Timing and Lattice Attacks,” 29th USENIX Security Symposium, August 12–14, 2020, PP.2057-PP.2073.
sec20-moghimi-tpm.pdf (usenix.org) - Arthur, Will, Challenger, David, and Kenneth Goldman, “A Practical Guide to TPM 2.0: Using the Trusted Platform Module in the New Age of Security”, Published by Apress in 2015.
- Milan Stanojevic, “TPM 1.2 vs. 2.0: Here’s everything you need to know”, TPM 1.2 vs 2.0: Here’s everything you need to know (windowsreport.com)
- PUFcc Introduction: PUFcc | High Security Crypto Co-Processor | PUFsecurity
- Chung, Sam, “PUFcc: An Essential Security Coprocessor for RISC-V Designs,” PUFsecurity White Paper, August 2021
Footnotes
- SM2, SM3, and SM4:
https://www.oscca.gov.cn/sca/xxgk/2012-03/21/content_1002392.shtml - NIST SP 800-90B
https://csrc.nist.gov/publications/detail/sp/800-90b/final - NIST CAVP
https://csrc.nist.gov/projects/cryptographic-algorithm-validation-program - OSCCA
https://www.oscca.gov.cn/sca/xxgk/2012-03/21/content_1002392.shtml - RFC
https://datatracker.ietf.org/doc/html/rfc7539
