D&R Industry Articles
Articles for the Week of April 22, 2024
From a Lossless (~1.5:1) Compression Algorithm for Llama2 7B Weights to Variable Precision, Variable Range, Compressed Numeric Data Types for CNNs and LLMs
This paper attempts to address and reconcile two different issues: the existence of multiple numerical data formats (such as int8, bfloat16, fp8, etc., often non optimal for the application and not directly compatible with one another) and the necessity to reduce their bandwidth requirements, especially in the case of power hungry and slow DRAM.Articles for the Week of April 1, 2024

Embracing a More Secure Era with TLS 1.3
TLS 1.3 offers attractive speed and security improvement benefits that are hard to ignore. The handshake phase was sped up by removing one or more roundtrips (back and forth messaging between client and server) in TLS 1.3 – with “or more” meaning that for certain cases, roundtrips can be entirely eliminated (0-RTT).Articles for the Week of March 25, 2024
Additional Articles- New PCIe Gen6 CXL3.0 retimer: a small chip for big next-gen AI
- Maximizing ESD protection for automotive Ethernet applications
Articles for the Week of March 18, 2024

Time Sensitive Networking for Aerospace
This white paper highlights the integration of Time-Sensitive Networking (TSN) in the aerospace industry. It provides an overview of TSN standards and profiles and the IEEE P802.1DP standard relevant to aerospace applications. It also discusses key topics such as time synchronization, latency, resource management, and reliability in the context of TSN.Articles for the Week of March 11, 2024

Understanding mmWave RADAR, its Principle & Applications
we will review and understand the technical aspects, application aspects, some mmWave RADAR concepts, estimation techniques, and MIMO concept. We will also look at different implementation platforms for RADAR estimation DSP part.Articles for the Week of March 4, 2024
Maximizing Performance & Reliability for Flash Applications with Synopsys xSPI Solution
Systems using SoCs designed in advanced processes generally rely on external Flash devices that use NOR/NAND Flash memory technology for non-volatile storage. NOR Flash memory offers many benefits for device manufacturers and consumers, such as faster reading, low power consumption, and smaller area. In contrast, NAND Flash memories are ideal for applications such as data storage, where higher memory capacity and faster write and erase operations are required.Articles for the Week of February 19, 2024
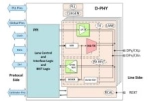
MIPI deployment in ultra-low-power streaming sensors
This article focuses on low-power scenarios with streaming sensors connected to a processor via MIPI. After a short overview of low-duty cycle sensor principles, we explore how a streaming image sensor leverages those principles, show how one semiconductor company uses MIPI CSI-2® and D-PHY interfaces in their imaging solution, and touch on use cases for ultra-low-power streaming sensors deploying MIPI.Articles for the Week of February 12, 2024
Design-Stage Analysis, Verification, and Optimization for Every Designer
An innovative approach that is rapidly gaining popularity in semiconductor design is the introduction of “shift left” analysis and verification, shifting signoff-quality design analysis, verification, and optimization back into earlier stages of the design flow. Calibre shift left solutions provide innovative tools and functionality that rely on proven, foundry-trusted Calibre rule decks and engines, ensuring the highest quality of results, industry-leading performance, and user-friendly integrations and interfaces.Articles for the Week of February 5, 2024

ASICs Bring Back Control to Supply Chains
OEMs must take back control of supply chains and consider taking an ASIC (application-specific integrated circuits) route, using cost-effective custom silicon designs, which can give back the flexibility, visibility, stability and resilience that supply chains need.- SignatureIP's iNoCulator Tool - a Simple-to-use tool for Complex SoCs
- Reducing Power Hot Spots through RTL optimization techniques
Articles for the Week of January 29, 2024
FinFET Technology and Layout
FinFETs form the foundation for many of today’s semiconductor fabrication techniques but also create significant design concerns that affect your layout. Understanding the changes and design strategies that finFET requires is crucial to building an effective layout. In this post, we’ll talk about how these changes influence integrated circuit layout.